ACL Rule Types
ACL rules can be applied to various components such as records, tables, and fields.
Record ACL rules
Record ACL rules include table and field names.
- A table name specifies the table to secure. If it has extending tables, then this table is called a parent table. The ACL rules for a parent table work for its child tables as well.
- A field name specifies the field to secure. As a result of table extension, some tables share the same fields. The ACL rule for a field in a parent table works for the same field in child tables as well.
ACL rules can restrict access to the operations listed in the following table. See the ACL article to learn more.
| Operation | Description |
|---|---|
| Create | Allows users to insert new records into a table. |
| Read | Allows users to display records from a table. |
| Write | Allows users to update records in a table. |
| Delete | Allows users to remove records from a table. |
The ACL rules are processed in the following order:
- Table ACL rules.
- Field ACL rules.
This order establishes a hierarchy: first, the users gain access to a more general object, and then to a more specific one. To access a record, the users must match to both table and field ACL rules.
- If a user has no access right to the table by the ACL rule, the access to all fields in the table is denied, even if the user meets the field ACL rule conditions.
- If a user has an access right to the table by the ACL rule, but has no access right to table fields based on the field ACL rule, the access to the fields is denied.
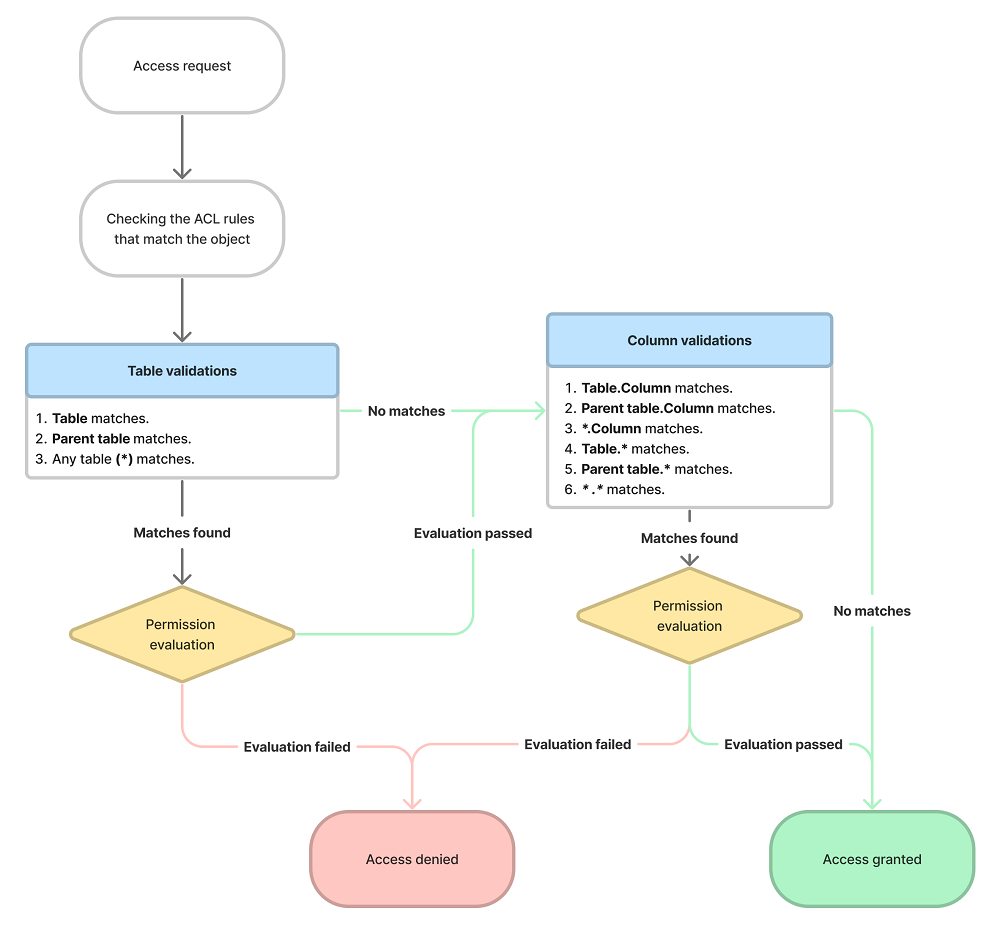
Table ACL rules
First, a user should match the conditions of the table ACL rule. The system includes wildcard (*) ACL rules that match any table or column. So the user should always match at least one table ACL rule. The access to the specific tables is secured by additional table ACL rules.
Table ACL rules are processed in the following order:
- Table. For example, Incident.
- Parent table. In the given example, it is the Task table.
- Match any table name (*).
If a user does not meet any table ACL rules, the access is restricted to all the fields in any tables. If the user meets the table ACL rule, they are to meet the field ACL rules.
Field ACL rules
When a user matches the table ACL rule, the field ACL rules are processed in the following order:
- Table and column name. For example, incident.number.
- Parent table and column name. For example, task.number, parent table of the Incident table.
- Any table and column name. For example, *.number.
- Table and any field. For example, incident.*.
- Parent table and any field. For example, task.*.
- Any table and any field. For example, *.*.
The users should match the field ACL rule; otherwise, the access to the table fields is denied. For example, a user wants to access the Number field in the Incident table. In this case, the user must first pass the table ACL rule.
If the user matches the first field ACL rule, the ACL check stops at the column level: the system stops searching other matching field ACL rules. For example, if a user meets the conditions of the field ACL rule for incident.number, the system stops searching for other ACL rules that secure the Number field in the Incident table, so only step 1 is performed.